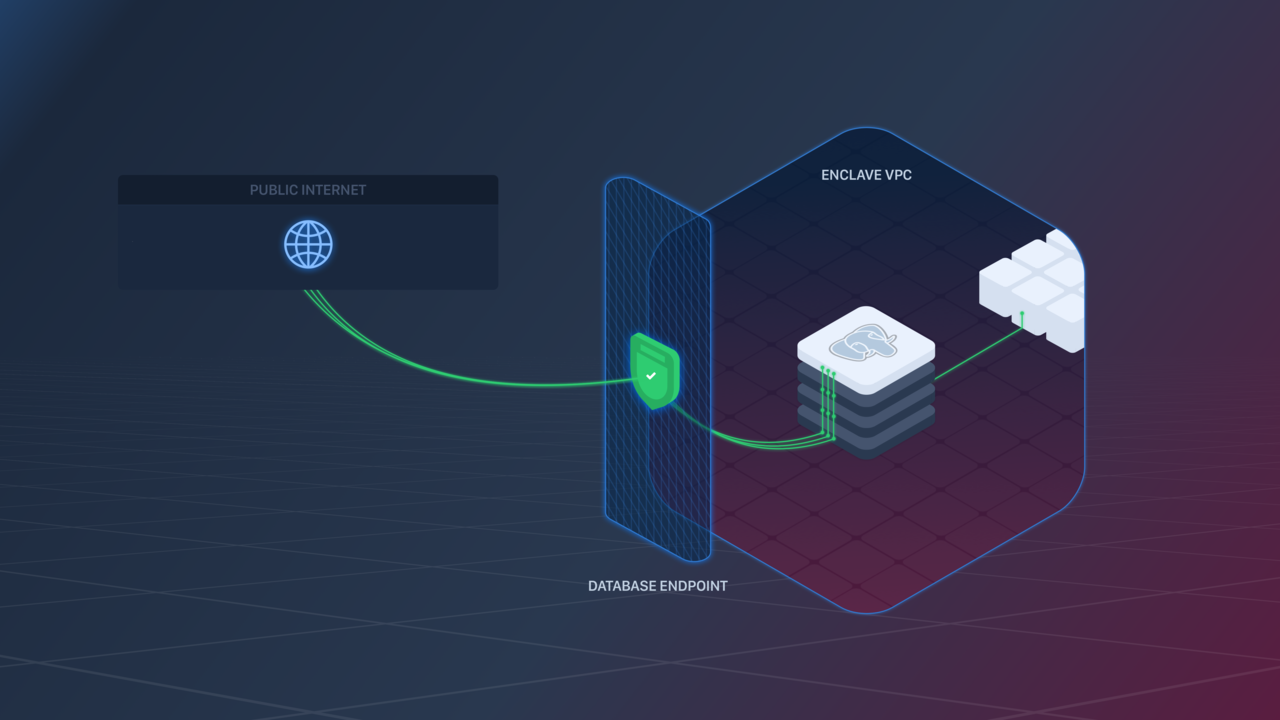
The underlying AWS hardware that backs Database Endpoints has an idle connection timeout of 60 minutes. If clients need the connection to remain open longer they can work around this by periodically sending data over the connection (i.e., a “heartbeat”) in order to keep it active.
Creating a Database Endpoint
Creating a Database Endpoint
A Database Endpoint can be created in the following ways:
- Within the Aptible Dashboard by navigating to the respective Environment >selecting the respective Database > selecting the “Endpoints” tab > selecting “Create Endpoint”
- Using the
aptible endpoints:database:createcommand - Using the Aptible Terraform Provider
IP Filtering
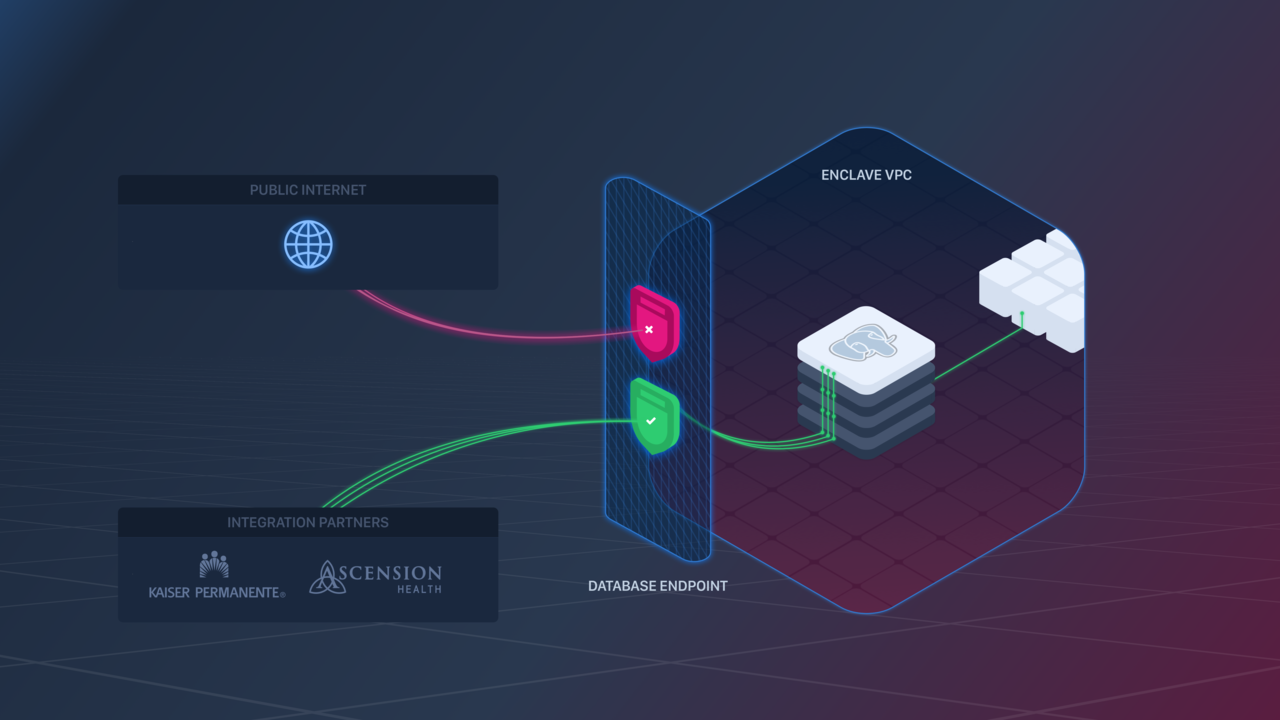
Configuring IP Filtering
Configuring IP Filtering
IP Filtering can be configured in the following ways:
- Via the Aptible Dashboard when creating an Endpoint
- By navigating to the Aptible Dashboard > selecting the respective Database > selecting the “Endpoints” tab > selecting “Edit”
Certificate Validation
To ensure that you connect to the Database you intend to, you should ensure that your client performs full verification of the server certificate. Doing so will prevent Man-in-the-middle attacks of various types, such as address hijacking or DNS poisoning. You should consult the documentation for your client library to understand how to ensure it is properly configured to validate the certificate chain and the hostname. For MySQL and PostgreSQL, you will need to retrieve a CA certificate using theaptible environment:ca_cert command in order to perform validation. After the Endpoint has been provisioned, the Database will also need to be restarted in order to update the Database’s certificate to include the Endpoint’s hostname. See the Database Encryption in Transit page for more details.
If the remote service is not able to validate your database certificate, please contact support for assistance.

